Empirical Research in the Internet of Things, Mobile Privacy, and Digital Advertising
In the world of consumer privacy, including the Internet of Things (IoT), mobile data, and advertising technologies (“Ad Tech”), it can often be difficult to measure real-world impact and conceptualize individual harms and benefits. Fortunately, academic researchers are increasingly focusing on these issues, leading to impressive scholarship from institutions such as the Princeton Center for Information Technology Policy (CITP), Carnegie Mellon University School of Computer Science, UC Berkeley School of Information, and many others, including non-profits and think tanks.
At events like the Privacy Law Scholars Conference, recently held in Washington, DC (PLSC 2018, May 30-31), privacy-minded scholars from around the world and across disciplines meet to share their research and new ideas each year. Many other conferences sponsor and call for technical privacy research, such as the Privacy Enhancing Technologies Symposium (PETS), which recently announced its accepted papers for 2018. Empirical studies from privacy researchers such as these are an invaluable part of having reasonable and concrete policy debates.
Here is some of the latest in technical and empirical privacy research from 2018:
Internet of Things and Smart Homes:
- User Perceptions of Privacy in Smart Homes – by Serena Zheng, Marshini Chetty, and Nick Feamster, Princeton University (2018)
- Researchers conducted semi-structured interviews with owners of smart homes, to explore “privacy awareness, concerns, and behaviors.” They found that: “first, convenience and connectedness are priorities for owners of smart homes, and these values dictate their privacy opinions and behaviors. Second, user opinions about who should have access to their smart home data depend on the perceived benefit. Third, users assume their privacy is protected because they trust the manufacturers of their IoT devices. Our findings bring up several implications for IoT privacy, which include the need for design for privacy and evaluation standards.”
- An Analysis of Home IoT Network Traffic and Behaviour – by Yousef Amar, et al, from the Queen Mary University of London, Imperial College of London, and University of Nottingham (2018)
- In this study, the authors set up six common IoT devices, and observed network traffic in order to assess privacy and security risks of home devices, as well as study their effects on bandwidth and power consumption. Readers interested in this topic should also check out an oft-cited paper presented at FTC’s 2016 PrivacyCon: A Smart Home is No Castle: Privacy Vulnerabilities of Encrypted IoT Traffic, by Noah Apthorpe, Dillon Reisman, and Nick Feamster (Princeton University).
- Clearly Opaque: Privacy Risks of the IoT (May 2018) – by The Internet of Things Privacy Forum
- Based on workshops and interviews with 40 experts, practitioners and scholars (including from Future of Privacy Forum), this report explores the privacy challenges of connected devices and the emerging strategies to address them, including issues of transparency, consent, identifiability, emotional and bodily privacy, and the destabilization of boundaries. UC Berkeley’s Center for Long-Term Cybersecurity published a short white paper version of the research.
Apps and Mobile Devices:
- Every Move You Make: Exploring Practical Issues in Smartphone Motion Sensor Fingerprinting and Countermeasures – by Anupam Das (Carnegie Mellon University), Nikita Borisov (University of Illinois at Urbana-Champaign), and Edward Chou (University of Illinois at Urbana-Champaign)
- The authors explore “device fingerprinting” in the mobile environment, where mobile apps typically rely on non-cookie tracking tools (advertising identifiers), and users of mobile browsers can be more difficult to distinguish from each other than users of web browsers. Among other things, the authors “collect measurements from several hundred users under realistic scenarios and show that the state-of-the-art techniques provide very low accuracy in these settings.”
- Touch and You’re Trapp(ck)ed: Quantifying the Uniqueness of Touch Gestures for Tracking by Rahat Masood (UNSW, CSIRO Data61) et al.,
- In this paper, similar to the one above, the authors demonstrate a 90%+ success rate for re-identifying users on the basis of their mobile gestures. As we learn more about the use of mobile sensors for inferring behavior (for example, whether a user is intoxicated), fingerprinting of sensor data from mobile devices may become one of the next major considerations for consumer privacy.
- “Won’t Somebody Think of the Children” Privacy Analysis at Scale: A Case Study With COPPA by Irwin Reyes (International Computer Science Institute), Primal Wijesekera (University of British Columbia), Joel Reardon (University of Calgary), Amit Elazari (University of California – Berkeley), Abbas Razaghpanah (Stony Brook University), Narseo Vallina Rodriguez (International Computer Science Institute, IMDEA Networks), and Serge Egelman (International Computer Science Institute, University of California – Berkeley)
- Researchers from UC Berkeley and International Computer Science Institute, and University of British Columbia, have demonstrated a way to efficiently analyze network traffic for mobile privacy implications in 80,000 Android apps in the Google Play store.
Online Advertising (Ad Tech):
- I never signed up for this! Privacy implications of email tracking by Steven Englehardt (Princeton), Jeffrey Han (Princeton), and Arvind Narayanan (Princeton)
- Email marketers’ uses of third-party tracking tools is often less well understood than online and mobile advertising technology. In order to better understand and describe it, Englehardt et al created a body of emails by signing up for hundreds of commercial mailing lists, and monitored the subsequent web traffic upon opening those emails. Their work describes a complex email marketing ecosystem, stating: “Email tracking is pervasive. We find that 85% of emails in our corpus contain embedded third-party content, and 70% contain resources categorized as trackers by popular tracking-protection lists. There are an average of 5.2 and a median of 2 third parties per email which embeds any third-party content, and nearly 900 third parties contacted at least once.”
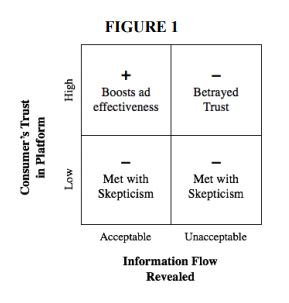
- Why Am I Seeing This Ad? The Effect of Ad Transparency on Ad Effectiveness by Tami Kim, Darden School of Business; Kate Barasz, IESE Business School; and Leslie K. John, Negotiations, Organizations, and Markets Unit at Harvard Business School.
- This research, published by the Harvard Business School and based off the lead author’s dissertation, investigates how and why ad transparency — the disclosure of ways in which personal data is used to generate personalized or behaviorally targeted ads — impacts the effectiveness of those online ads. The authors predict that “ad transparency undermines ad effectiveness when it exposes marketing practices that violate consumers’ beliefs about ‘information flows’–how their information ought to move between parties.” (p.2). Through experiments, the authors find supporting evidence that whether information flows are deemed acceptable depends on “the extent to which the ad is based on 1) consumers’ activity tracked within versus outside of the website on which the ad appears and 2) attributes explicitly stated by the consumer versus inferred by the firm (the latter of each pair is deemed less acceptable.” (p.38)
- ‘I’m supposed to see that?’ AdChoices Usability in the Mobile Environment by Stacia Garlach and Daniel D. Suthers, University of Hawai‘i at Mānoa, Proceedings of the 51st Hawaii International Conference on System Sciences (2018)
- In this paper, Stacia Garlach and Professor Daniel D. Suthers investigate a small sample of smartphone users, and explore whether and how they notice, understand, and use the “AdChoices” icon in typical mobile advertisements.
- Discrimination in Online Advertising A Multidisciplinary Inquiry – by Amit Datta, Carnegie Mellon University, Anupam Datta, Carnegie Mellon University, Jael Makagon, UC Berkeley, Dierdre K. Mulligan, UC Berkeley, and Michael Carl Tschantz, International Computer Science Institute, Proceedings of Machine Learning Research 81:1–15, 2018
- In this paper, Datta et al explore the ways in which discrimination may arise in the targeting of job-related advertising. Under Section 230 of the Communications Decency Act, which provides interactive computer services with immunity for providing access to information created by a third party, the authors argue that “such services can lose that immunity if they target ads toward or away from protected classes without explicit instructions from advertisers to do so.”
Did we miss anything? Send us your recommended research and scholarship at [email protected]
Several papers listed above are accepted papers for the 2018 Privacy Enhancing Technologies Symposium (PETS) (July 24-27, 2018).
EDITED 6/13/18 to add a recent report, Clearly Opaque: Privacy Risks of the IoT (May 2018), by The Internet of Things Privacy Forum