FPF & Dataskydd.net Webinar – Privacy in High Density Crowd Contexts
Authors: Hunter Dorwart and Rob van Eijk
On 30 September 2020, Future of Privacy Forum (FPF) and Dataskydd.net jointly organized the webinar ‘Privacy in High Density Crowd Contexts’. A key aspect of the webinar was the role of industry-driven privacy standards in the development and deployment of privacy-friendly technologies for crowd management, mobile connectivity, and smart city services.
Keywords: IEEE P802E Recommendations, Privacy by Design, Certification, Standardization
Speakers (in alphabetical order)
- Amelia Andersdotter (Dataskydd.net, Member of the European Parliament 2011-2014)
- Jelena Burnik (Head of International Cooperation and Enforcement at the Information Commissioner of the Republic of Slovenia)
- Jerome Henri (Cisco, Editor P802E)
- Kelsey Finch (Future of Privacy Forum)
- Marit Hansen (State Commissioner for Data Protection Schleswig-Holstein)
- Rob van Eijk (Future of Privacy Forum)
- Tiago Rodrigues (Wireless Broadband Alliance)
- Udo Oelen (Chief Privacy Officer at Dutch Railways, former Head of Private Sector at the Dutch Data Protection Authority)
The recording is available here.
Privacy-Preserving Technologies and Standards Development
Many industry-driven standards development organizations (SDOs) have been working to improve the general privacy qualities of both network infrastructures and web infrastructures. Generally speaking, these bodies focus on how industry standards can remedy design flaws in technologies in order to facilitate transparency, foreseeability, and the ability of consumers to both opt out and make decisions about the way they can interact with technical infrastructures.
Some of these standards have been quite successful and continue to show a lot of promise to address emerging privacy issues in technology. For instance, the Internet Engineering Task Force (IETF), which is responsible for the bulk of what consumers see in a web browser or in an email, considers privacy issues when developing Internet standards through, among other things, the RFC6973 Privacy Considerations for Internet Protocols. In addition, many technical bodies are attempting to introduce encryption and minimization standards to ensure that network protocols do not generate identifiers beyond what is necessary for the network to function.
As the world becomes more digitized, SDOs will continue to develop privacy-preserving standards. However, challenges are beginning to emerge regarding the widespread adoption of these standards and how industry-setting bodies such as Internet Engineering Task Force (IETF), the Institute of Electrical and Electronics Engineers (IEEE), 3rd Generation Partnership Program (3GPP), and the World Wide Web Consortium (W3C) interface with EU-level policymaking. As it is, there is a real risk that the underlying policy goals of governments may conflict with future standards setting and that lack of coordination across SDOs and between governments may hinder consistency and interoperability.
Striking a balance between protocols that need some type of identifier to function and the level of privacy exposure that might result has created difficulties for embedding privacy within standards. In order to enable seamless communication between routers and devices, protocols that govern access points within the routers must trace identifiers unique to a product device. Because devices are often linked to an individual user, the network protocols that facilitate communication invariably expose data about these users. The IEEE navigates this trade-off by providing technical solutions to help developers make this seamless flow of communication and data-sharing more aligned with public policy goals.
IEEE Recommended Practices for Privacy Considerations for IEEE 802 Technologies
To this end, the IEEE P802E working group has been drafting Recommended Practices for Privacy Considerations for IEEE 802 Technologies (P802E). P802E contains recommendations and checklists for IEEE 802 technologies developers (Figure 1). The approach builds on Section 7 questionnaires of RFC6973 Privacy Considerations for Internet Protocols adapted to the IEEE 802 environment which considers harms and risks to privacy when developing network protocols.
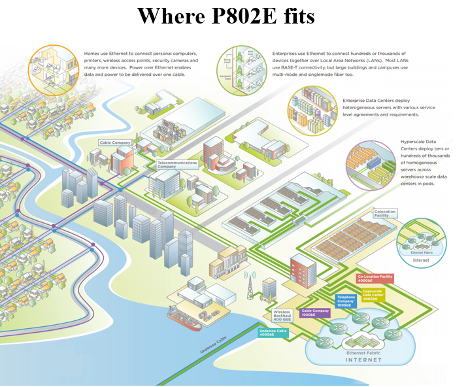
Figure 1 – Overview of P802E applications (slide from the presentation by Jerome Henry)
The purpose of the P802E recommendation is ‘to promote a consistent approach by IEEE 802 protocol developers to mitigate privacy threats identified in the specified privacy threat model and provide a privacy guideline.’ In order to strike the right balance between functionality and privacy, the IEEE focuses on the context of device use. For instance, personal devices make it easier to identify the user through network traffic routing while shared devices generally do not. The rubric for developing standards therefore changes depending on how users will interface with the device.
IEEE 802 LAN standards specify the operation of media access control (MAC) methods and protocols that support frame-based network communication. MAC procedures and various protocol frame formats and fields can be used to identify personal devices, their attributes, and their use to support specific networking applications and activities. An adversary can use this information to obtain (location) information about an individual. Other possible threats in IEEE 802 LAN standards are, e.g., flow identifiers, optional fields in the standard, network discovery flows and patterns, ranging exchanges, authentication flows, directed queries, frame timing, and frame structure. Figure 2 illustrates the threat of location services systematically tracking (mobile) access points.
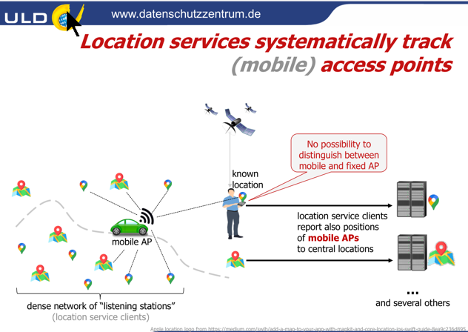
Figure 2 – Example of the threat of location services systematically tracking (mobile) access points (slide from the presentation by Marit Hansen).
Speed to Market
As standards evolve, policymakers and industry must work together to minimize the speed to market. This includes facilitating the adoption of privacy by design and establishing appropriate benchmarks for matching regulatory compliance with technological design. As it is, one major challenge facing public-private partnerships is how fast the technological landscape changes. Putting in place the infrastructure to adapt standards to novel privacy challenges becomes difficult as more IoT devices proliferate throughout the economy and make tracking scenarios much larger than before.
Standardization and Certification
From the perspective of industry, many stakeholders in the broadband industry see the importance of implementing privacy policies throughout their services and recognize the demand from policymakers. Like standards bodies, network operators must also strike a balance between functionality and privacy-preserving practices. But this doesn’t have to be a zero-sum tradeoff. Organizations can push for policies that establish a compliance baseline that industry must meet. In turn, this enables standards bodies to have a better sense of how to build trust chains for authenticated communications in particular environments.
To this end, technical standardization is an important and valid tool for building compliance and achieving common knowledge and common understanding around emerging technologies. Furthermore, in the EU, codes of conduct and certification (article 40-43 GDPR) complement the toolkit. However, even though policymakers can establish benchmarks through regulations, it is still necessary to engage with industry and technical bodies in order to clarify ambiguities in the law. While standards can serve as benchmarks for DPAs and relevant authorities, there needs to be a relevant mechanism to ensure transparency in the auditing process and validate that market players are really respecting the standard.
Lessons Learned from Smart Cities and Transportation
Current discussions around automotive and transportation use-cases illustrate some of these lessons. When designing automotive technology to connect cars to smart devices, engineers have had to adjust to changing regulatory and market environments. Back in the mid-2000s, car designers relied on device identifiers to connect mobile phones to cars. But now that the environment has changed, engineers have come up with new ways to ensure connectivity without having to rely on identifying a particular user to a device.
As standards around identifiers continue to change, so too will the technology in automobiles. Widespread adoption in the market of new technologies is not just a technical challenge but also an industry challenge. Industry must be ready to embrace the new technical features, which means the question becomes one of measuring the demand needed to change industry behavior.
Policymakers can contribute to this through implementing regulatory initiatives and engaging with industry and technical bodies. For instance, in the EU, any processing of data around wifi and device identifiers needs to comply with the GDPR. In part, this baseline establishes a legal basis for smart cities to process mobility data and can serve as a target for standards development bodies in their activities.
For instance, Dutch Railways faced issues around data processing for crowd management purposes. While facilitating public transportation qualifies as a legitimate interest to process data under the GDPR, railway operators must check whether the way they process crowd data is really the best option and valid under the circumstance. Indeed, Dutch Railways faced many issues around crowd management and had options to enable both wifi and bluetooth tracking to process data, but chose to take a method that was less privacy intrusive than alternatives. They utilize(d) wifi tracking only in locations where absolutely necessary and trace travel patterns of commuters with an alternative method that masks the identities of the passengers.
Dutch Railways does this by hashing twice the WiFI-MAC address of the traveler’s phone through sensors in the railway station and sending the data to a central server. During the length of commute, subsequent sensors send hashed information to the same server which allows the company to match the data and generate a mobile pattern while preserving the identity of the commuter. The data is available for only one day before it is deleted which minimizes the risk of aggregating large data sets over time.
In addition, in the context of smart cities, it’s also important for policymakers and city coordinators to communicate effectively with the public. For instance, while there isn’t a clear legal standard for processing mobility data in the United States, public backlash about wifi tracking throughout cities serves as an incentive not only for policymakers to adopt more privacy-preserving trafficking solutions but also for industry to enable those solutions through product design. Organizations therefore need to engage with the public in a meaningful way to effectuate problem solving.
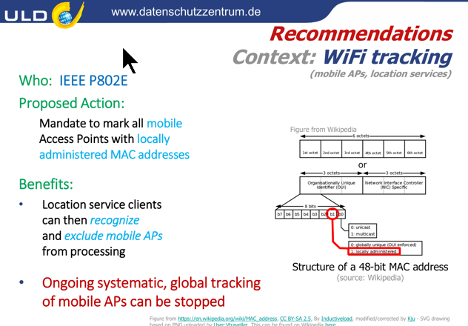
Figure 3 – Recommendations aimed at the use of MAC addresses in the context off Wi-Fi tracking (slide from the presentation by Marit Hansen).
Takeaways from the Panel Discussion
P802E defines a framework, a recommended practice for privacy considerations when designing or evaluating an IEEE 802 Standard. P802E does not provide a standard-specific set of rules or recommendations. The goal of the framework is to encourage designing for privacy, limiting (unauthorized) personal information exposure as much as possible. P802E can be used beyond 802 technologies, to inform how privacy may be affected by networking communications in the Data Link Layer (also known as L2-layer). The L2-layer is the second level in the seven-layer OSI reference model for network protocol design.
Different contexts (e.g., hospital, public Wi-Fi tracking, airport, smart city transportation platform) imply different privacy requirements which means that stakeholders need to communicate the privacy policies expectations for each vertical transparently. Mobile users expect a harmonized experience across contexts, which creates challenges for public sector actors, private industry, certification bodies, and technical standards bodies to strike the right balance between functionality and privacy.
When developing standards, SDOs should explore how such standards fit in regulatory regimes and the specific rules and definitions of personal data. Policymakers in turn must search for synergies to promote compliance with various legislative and regulatory rules and engage with standards bodies to ensure that stakeholders are on the same page. Such engagement should reflect a broad, interconnected way of thinking and routinely employ use cases to find the appropriate technical solution. To this end, it is also important that organizations involved in these workstreams know and appreciate the same terminology and frameworks.
Following such a path could help shorten the speed to market and ensure that technical standards and certification schemes are flexible and adaptive to the vast changes in technology that confront us.
The recording is available here.
To learn more about FPF in Europe, please visit fpf.org/eu. For information about Dataskydd.net click here.



