Understanding Blockchain: A Review of FPF’s Oct. 29th Digital Data Flows Masterclass
Authors: Hunter Dorwart, Stacey Gray, Brenda Leong, Jake van der Laan, Matthias Artzt, and Rob van Eijk
On 29 October 2020, Vrije Universiteit Brussel (VUB and Future of Privacy Forum (FPF) hosted the eight Digital Data Flows Masterclass. The masterclass on blockchain technology completes the VUB-FPF Digital Data Flows Masterclass series.
The most recent masterclass explored the basics of how blockchain technologies work, including established and proposed use cases, which were then evaluated through the lens of privacy and data protection. How does blockchain technology work? Does blockchain present opportunities for a privacy-by-design approach? What is the legal compliance analysis of blockchain systems, particularly addressing the roles and responsibilities of various parties engaging with the technology?
FPF’s Brenda Leong and Dr. Rob van Eijk moderated the discussion following expert overviews from Jake van der Laan (Director Information Technology and Regulatory Informatics at the Financial and Consumer Services Commission of New Brunswick) and Dr. Matthias Artzt (Senior Counsel, Deutsche Bank).
The slides of the presenters can be accessed here and here.
The recording of the class can be accessed here.
Blockchain Technology – What is it and how does it function?
The term blockchain refers to a distributed ledger technology, composed of recorded transactions in set groupings, called “blocks,” that are linked to each other using cryptographic hashes. These linked blocks form the “chain” (Figure 1), and if any block is tampered with after it’s been added to the chain, that change would be immediately noticeable because the hashed link would be broken (would no longer match between the two blocks).
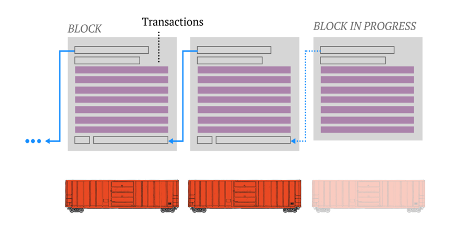
Figure 1. Analogy of a train for chaining together blocks of transactional information.
Additional blocks of information (e.g., recorded transactions) get added to the ledger when they receive verification from other blocks that they have successfully solved an accompanying mathematical challenge (by “miners”). This verification process takes several minutes, but once 51% of the participating nodes have verified the result, the block is permanently added to that chain.
Because these transactions are simultaneously recorded on ledger systems in independent locations around the world (called “nodes”), all copies of which are updated at the same time when a new transaction is recorded, the security of information recorded on a blockchain is considered “immutable” or unchangeable (Figure 2). Originally designed specifically to manage a cryptocurrency system such as Bitcoin, the point of this process was to enable trust and reliability within a system without a central manager, like a bank or national financial system.
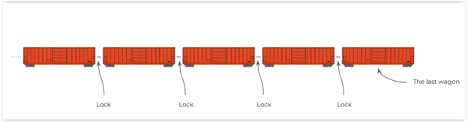
Figure 2. The information contained in the records are extremely resistant to alteration.
Expanding Use Cases
Although initially, blockchain systems were used only for cryptocurrencies, this technology can potentially be used for other purposes. Blockchain was initially designed to alleviate the need for a manager or controlling entity, recording transactions for anonymous or pseudonymous users, and with the expectation that all related information was included in the transaction as stored on the chain. However, as the underlying technology has been considered for other uses, there have been a number of changes to that design.
Distributed ledgers are now created in ways that can be private, public or hybrid in nature. Public ledgers operate as an open network which allows anyone to download the protocol and participate in the network. Private ledgers, by contrast, work on an invite-only basis with a single entity governing the network. Hybrid systems combine elements of these two systems. In part, blockchains vary in the degree to which type of ledger they create as well as what activity the ledger specifically records.
Blockchain has in recent years been considered for applications such as supply-chain management; recording or property or real estate records; smart contracts; and even voting functions. One of the leading commercial providers of blockchain systems, Ethereum is a global, open-source platform for many decentralized applications. The full usefulness of blockchain for such applications is not yet fully understood, and many use cases are still being developed or explored.
Legal Implications of Blockchain for Privacy and Data Protection – Roles and Responsibilities
Blockchain technology raises many privacy and legal implications that warrant awareness from industry professionals, policymakers, and the general public. When a blockchain ledger is used to manage or even directly store personal information, the processing of that personal information will fall under the auspices of most privacy and data protection laws, including the General Data Protection Regulation (GDPR).
Those managing or using a blockchain-based system could assume certain responsibilities depending on their role in processing the data. Under the GDPR, a “controller” means “the natural or legal person, public authority, agency or other body which, alone or jointly with others, determines the purposes and means of the processing of personal data.” Art. 4(7). “Processors” refer to a natural or legal person, public authority, agency or other body which processes personal data on behalf of the controller.” Art. 4(8).
Dr. Artzt described the roles and the responsibilities of blockchain participants under the GDPR and similar international data protection regimes.
- Miners validate transactions by solving a mathematical puzzle defined by the applicable consensus mechanism used by the blockchain. Miners do not determine the specific purpose of any data processing activity nor do they carry out any specific services based on instructions of controllers. Therefore miners are not controllers or processors under the GDPR.
- Nodes refer to the decentralized computers that each store a copy of the blockchain. As an IT operation, storing does not implicate decision-making processes. Therefore nodes are not controllers or processors. Indeed, it is difficult to interpret merely participating in the blockchain network as determining the means and purpose of a specific data processing activity.
- Wallets store and manage asymmetric keys and addresses used for transactions at the application level. Wallets allow blockchain users to control their own private keys and interact with the network. As a software package, wallets merely pass data from users to miners and therefore do not by themselves determine the purpose or means of processing and are not controllers.
- Users – Users participate in transactions on a blockchain network. Users could be controllers if (i) personal information is submitted to the ledger and (ii) the processing activity has a professional or commercial background only. However, if the processing of information is in the course of a “purely personal or household activity,” it may fall under the GDPR’s household exception. Art. 2(2)(c). In that case, the GDPR doesn´t apply.
- Smart Contract Developers create algorithms to use in “smart contract” programs stored on the blockchain which provide certain functionality to blockchain users. Notably, they do not operate the software they write and therefore do not determine the purpose and means of the processing activity.
- Oracles refer to agents that allow the transfer of external data feeds to the blockchain to leverage smart contracts. Oracles are necessary to process external real-world events for the network and have a strong influence on the data processing operation. Therefore, oracles can qualify as controllers if they have a commercial interest in the outcome of the related data processing.
- Governance Bodies monitor blockchain transactions and define the roles of the participants. Existing only in private blockchains, a governance body qualifies as a controller if it has control over the processing of personal data. Governance bodies can also determine one participant to act as a controller and become processors or joint controllers as a result.
Data Subject Rights, Minimization and Purpose Limitation
Because storage counts as data processing under the GDPR and new uses of blockchain technology involve some direct storage of data, the use of the technology raises other privacy implications and trade-offs. Clarifying the nature of these implications will be increasingly important not only for users and operators of blockchain but also for policymakers who must ask difficult questions about the appropriate scope of regulation. For this reason, our speakers recommended that a best practice would include storage of personal data off-chain, or remove personal data which is not needed any more (“legacy data”) from the blockchain, storing it in an external database off-chain and link the stored information to the recorded exchanges and transactions via on-chain hashes
From the discussion, data subjects exercising their rights – such as the right to deletion – under the GDPR may run into problems determining who should respond to such requests. Here, the distinction between public and private blockchains becomes critical. With private blockchains, a data subject may theoretically treat the governance body as the responsible controller of their information. But with public blockchains, the data subject faces the dual challenge of identifying the appropriate controller and ensuring the controller carries out its obligation.
What’s more, the nature and design of the technology itself compounds such challenges by making it nearly impossible to access or modify the information contained in the blockchain. For instance, a controller in a public blockchain won’t be able to comply with data subject access requests as a matter of feasibility. Any data on the public blockchain will be there to stay and can’t be deleted or rectified.
Similarly, the immutability of data in blockchains creates tension with other data privacy principles such as purpose limitation and data minimization. By nature, blockchain continuously processes data, forever recording information related to the full history of past transactions.. This makes it practically impossible to minimize data use to that which is necessary for a particular transaction.
Techniques to Mitigate Data Protection Risks
In some cases, the data protection challenges of complying with data subject rights and other legal obligations can be mitigated through the use of private blockchains; off-chaining the data; and innovative encryption techniques, e.g. hashing.
Adopting a private blockchain resolves certain issues because the governance body has more control and is better equipped to respond to data subject requests. Such a solution impacts the utility and scalability of the technology. The fundamental problem with the immutability of the blockchain is the perpetual storage of information.
Creating a mechanism for the use of legacy data may provide one legal solution to this issue. In one scenario, legacy data from a mutable private blockchain where the real-time processing takes place could be transferred to an immutable public blockchain through interoperating multi-layered blockchains.
The most straightforward and efficient technique for resolving the issue with legacy data is the hashing-out approach: Legacy data is removed (hashed-out) from the blockchain and put externally (off-chain). The personal data is replaced with a hash value which remains on the blockchain and points to the reference data stored externally. In the case of a deletion request raised by an individual, the off-chain personal information can be deleted.
Off-chain storage may resolve some of the issues around erasure requests and enable greater data minimization and purpose limitation. Once the controller deletes the corresponding personal data in the external database, the hash value remaining on the blockchain becomes a random string with no meaning. Because blockchain uses cryptographic hash functions, in most cases it is impossible to reverse engineer the original (reference) data from the hash. As a result, the hashed section is no longer tied to personal information, and therefore no longer subject to the same legal implications.
Under GDPR or similar legal frameworks, controllers will likely have to carry out a data privacy impact assessment (DPIA). Such an assessment provides an opportunity for controllers of a blockchain-based system to evaluate the appropriate technical and organizational measures they can adopt to minimize privacy risks. Utilizing various mitigation measures may offer controllers ways to apply privacy-preserving technical solutions while benefiting from potential innovative capabilities.
Because of the many unresolved privacy and regulatory questions around blockchain systems, policymakers and other stakeholders must be aware of the particular concerns and challenges involved with adopting this technology for new applications and use cases.
The slides of the presenters can be accessed here and here.
The recording of the class can be accessed here.
To learn more about the eight masterclasses in the VUB-FPF Digital Data Flows Masterclass series click here.
To learn more about FPF in Europe, visit https://fpf.org/eu.



