Showing results for viiia20 bobet bad credentials bobet

Code of Conduct / Anti-harassment Policy
[…] others involved in activities who violate this anti-harassment policy may be sanctioned or expelled from the activity at the discretion of the community organizers. Harassment and other bad behavior reduces the value of the programs for everyone. Unacceptable Behavior Harassment includes, but is not limited to: Verbal or written comments that reinforce social structures of […]
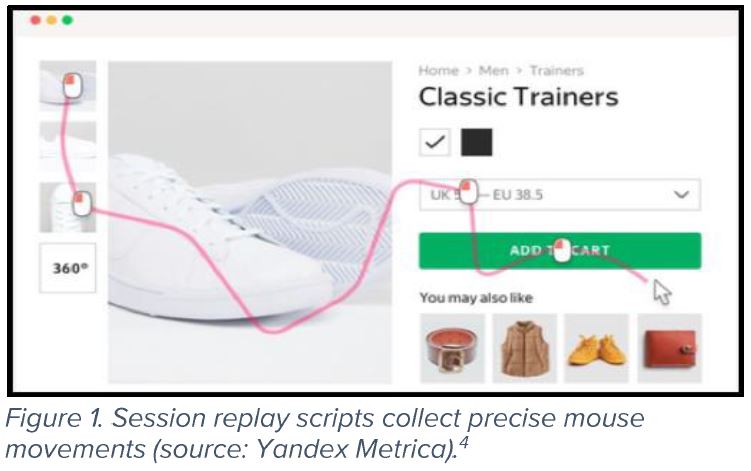
Understanding Session Replay Scripts – a Guide for Privacy Professionals
[…] Exfiltration of Personal Data by Session-replay Scripts, Freedom to Tinker (Nov. 12, 2017), https://freedom-to-tinker.com/2017/11/15/no-boundaries-exfiltration-of-personal-data-by-session-replay-scripts/. Arvind Narayanan, Website operators are in the dark about privacy violations by third-party scripts, Freedom to Tinker (Jan. 12, 2018), https://freedom-to-tinker.com/2018/01/12/website-operators-are-in-the-dark-about-privacy-violations-by-third-party-scripts/. Steven Englehardt, No boundaries for credentials: New password leaks to Mixpanel and Session Replay Companies, Freedom to Tinker (Feb. 26, 2018), https://freedom-to-tinker.com/2018/02/26/no-boundaries-for-credentials-password-leaks-to-mixpanel-and-session-replay-companies/.
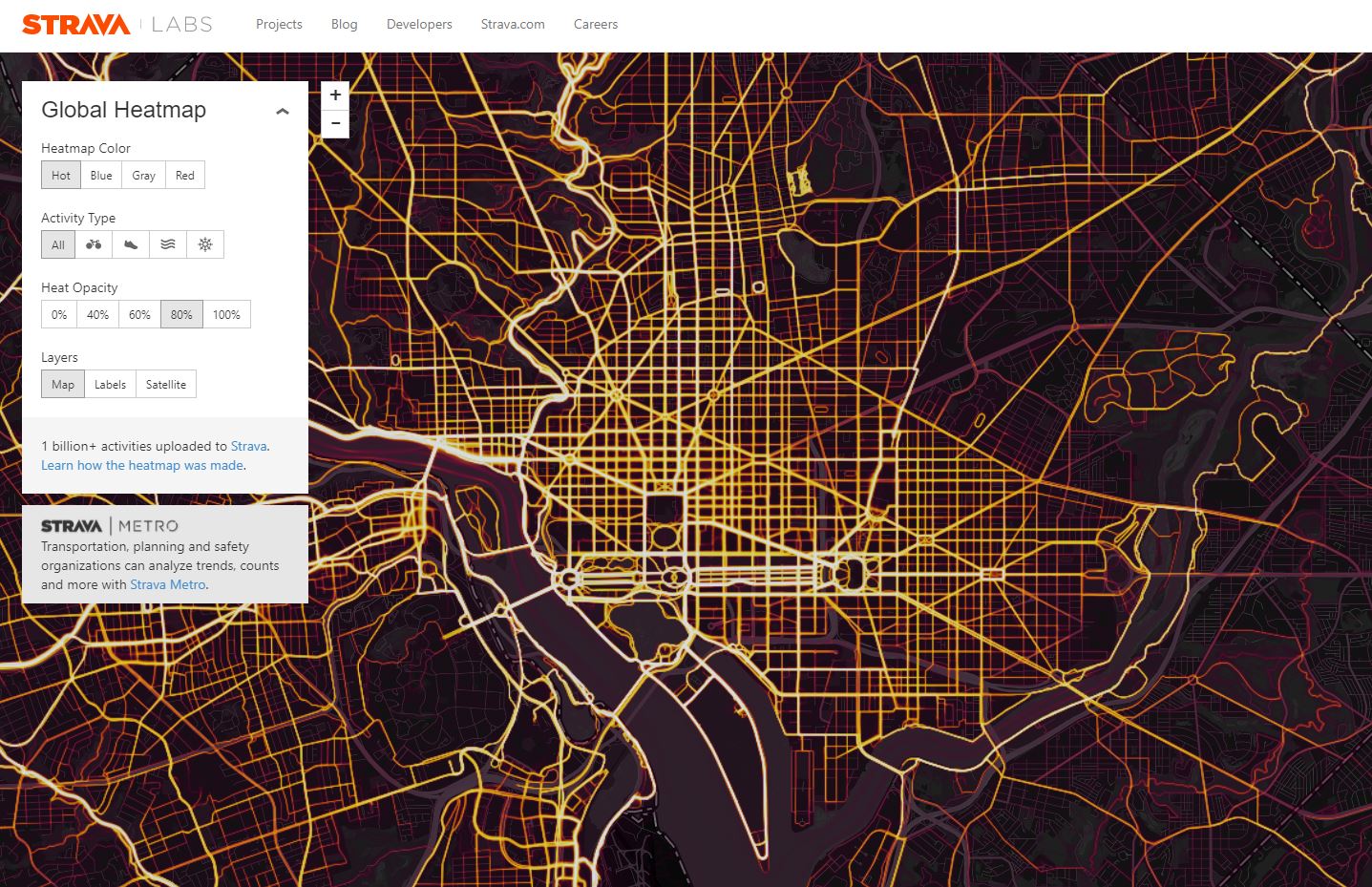
If You Can't Take the Heat Map: Benefits & Risks of Releasing Location Datasets
[…] out as “a map of rich white people.” Although the comment was likely offhand, the issues are serious — particularly in “smart” systems that use algorithmic decision-making, bad data can lead to bad policies. For example, both predictive policing and criminal sentencing have repeatedly demonstrated racial bias in both the inputs (historic arrest and […]

WashingTech Tech Policy Podcast’s Episode 107
[…] and policy now stand in light of recent data breaches. Jules also discussed what consumers can do to protect their data. Given the recent Equifax data breach, he explained the importance of freezing your credit to prevent bad actors from opening accounts in your name. Listen to the full interview at the link below. LISTEN

The Top 10: Student Privacy News (May – June 2017)
[…] of Education. There was a hearing on the CTA in the House, and many people continue to weigh in on whether the CTA is a good or bad idea. Following in the footsteps of the ACLU of Massachusetts, the ACLU of Rhode Island released their research on a lack of privacy protections in 1-1 programs in Rhode […]

WannaCry About Backdoors
[…] that we should have a back door. But the reality is if you put a back door in, that back door’s for everybody, for good guys and bad guys.” Strong encryption is permitted even under the 1994 U.S. law that requires phone companies to build their networks to respond to court orders. As the […]
FPF Comments on NHTSA’s V2V Rulemaking
Yesterday, the Future of Privacy Forum submitted written comments to the Department of Transportation and National Highway Traffic Safety Administration in response to their Notice of Proposed Rulemaking on Vehicle to Vehicle Communications.

Privacy Papers 2016
[…] expectations are far from idiosyncratic and arbitrary. Our work calls for approaches to providing access that are more judicious than a simple on/off spigot. Complex information ontologies, credentials of key actors (i.e. sender and recipients in relation to data subject), and terms of access – even lightweight ones – such as, identity or role […]
Samsung Electronics Vice Chairman Traveling to the United States for Internet of Things – Transforming the Future Conference
On June 21, 2016, Samsung will host its inaugural “Internet of Things – Transforming the Future” conference at the Washington Post, during which the company will lay out its vision for a human-centered approach to the Internet of Things (IoT) that focuses on the outcomes the technology will create for people and societies across the globe.

Should Colleges Report When They Get Government Data Requests?
[…] “By being too transparent, you could impede on students’ individual rights,” she told NBC News. Sharing information that could be used to identify students would be a bad idea, Leong said, but simply divulging the number of requests received and granted by a university would be a step in the right direction. Read the […]
