Showing results for planfully call 614 647 0039 electrical service planfully call 800 387 0073 614 647 0039 1-800-387-0073 call 614 647 0039 call 1 0073 614 647 0039 614 647 0039 800 387 0073 614 647 0039
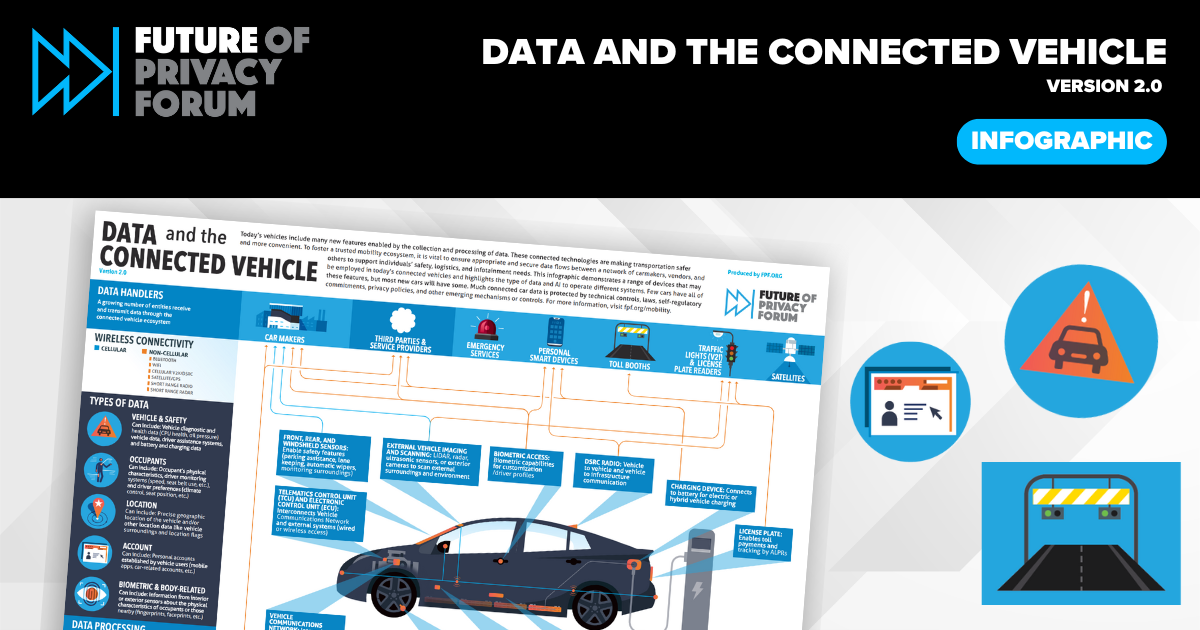
Updated FPF Infographic Explores Data in Connected Vehicles
[…] performance and safety. Once the data is collected, its transfer and use can depend on a number of factors, including agreements with the manufacturer, third parties and service providers, emergency services, and external infrastructure such as traffic lights and automatic license plate readers. Manufacturers may receive vehicle and safety data, location data, account data, […]

Infographic Explores Driver Data Collection and Use in Connected Cars
[…] an understanding of how their data is collected and used in connected vehicles and how data flows in the connected vehicle ecosystem. Individuals and policymakers have increasingly called for additional transparency regarding vehicle data and what happens with it. FPF’s updated Data and the Connected Vehicle infographic provides an accessible visual of the critical […]

FPF_connected_vehicl_v2_03_nosidebar (2)
[…] CAN BUS, Ethernet, LIN) DSRC RADIO: Vehicle to vehicle and vehicle to infrastructure communication BIOMETRIC ACCESS: Biometric capabilities for customization /driver profiles CAR MAKERS THIRD PARTIES & SERVICE PROVIDERS A growing number of entities receive and transmit data through the connected vehicle ecosystem DATA HANDLERS TRAFFIC LIGHTS (V2I) & LICENSE PL ATE READERS PERSONAL […]

Call for Nominations: 15th Annual Privacy Papers for Policymakers Award
[…] 9, 2024 —The Future of Privacy Forum (FPF) invites scholars and authors with an interest in privacy issues to submit finished papers to be considered for its 15th annual Privacy Papers for Policymakers (PPPM) Awards. The award provides privacy and data protection scholars, researchers, and authors in the U.S. and internationally with the opportunity […]

Privacy Roundup from Summer Developer Conference Season 2024
[…] Apple has announced major changes to Siri to support a more integrated user experience with two clear privacy protections for cloud-based AI. Apple’s first privacy protection is called Private Cloud Compute, which isolates computation to provide data protection during cloud-based computations. The details of this architecture are complex, but the goal is simple: to […]

FPF Highlights Intersection of AI, Privacy, and Civil Rights in Response to California’s Proposed Employment Regulations
[…] including decisions that materially impact access to, or approval for, housing or accommodations, education, employment, credit, health care, and criminal justice. Assembly Bill 2930 A system or service that uses artificial intelligence and has been specifically developed to, or specifically modified to, make, or be a substantial factor in making, consequential decisions. Role-Specific Responsibilities […]

Singapore’s PDP Week 2024: FPF highlights include a hands-on workshop on practical Generative AI governance and a panel on India’s DPDPA
[…] of Data Protection, Privacy, and Cybersecurity at Drew & Napier; and Lee Matheson, Senior Counsel for Global Privacy at FPF. The experts discussed strategies for selecting AI service providers, emphasizing the importance of internal policies and risk assessment. The panelists argued that while AI introduces new technologies and applications, it ultimately functions similarly to […]

CPDP LatAm 2024: What is Top of Mind in Latin American Data Protection and Privacy? From data sovereignty, to PETs
[…] Relatedly, panelists discussed use cases where PETs can help with business development while preserving the privacy and utility of the data. For instance, in the food delivery service industry, panelists discussed how different techniques help obscure or eliminate personal data retrieved from customer interactions. If properly implemented, businesses can keep relevant data for analysis […]

Contextualizing the Kids Online Safety and Privacy Act: A Deep Dive into the Federal Kids Bill
[…] would establish a two-part threshold for when companies are required to comply with various data protection obligations, such as access, deletion, and parental consent, for when a service is “directed to children” or when services have “actual knowledge” that an individual is a child. However, KOSPA would modify the standard in a novel way: […]
