Showing results for feifei phone number 1800 299 964 fpfgw 252 fpfgw 283 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 283 fpfgw 252 fpfgw 283 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 275 fpfgw 296 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 275 fpfgw 296 fpfgw 275 fpfgw 254 fpfgw 283 fpfgw 252 fpfgw 283 fpfgw 252 fpfgw 283 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 277 fpfgw 218 975 feifei phone number 860 490 8326 1800 299 964 860-490-8326 number 1800 299 964 fpfgw 252 fpfgw 283 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 283 fpfgw 252 fpfgw 283 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 275 fpfgw 296 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 275 fpfgw 296 fpfgw 275 fpfgw 254 fpfgw 283 fpfgw 252 fpfgw 283 fpfgw 252 fpfgw 283 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 277 fpfgw 218 number 860 8326 1800 299 964 1800 299 964 252 283 254 275 254 275 254 283 252 283 254 275 296 275 296 275 254 275 254 275 254 275 296 275 296 275 254 283 252 283 252 283 254 275 254 275 296 277 296 275 254 275 254 275 254 275 254 275 296 277 296 277 218 975 860 490 8326 1800 299 964

Privacy Scholarship Research Reporter: Issue 2, July 2017 – Artificial Intelligence and Machine Learning: The Privacy Challenge
[…] problems of three basic types: (1) data privacy problems; (2) boundary management problems; and (3) social/relational problems. Technological design can ward off, if not fully prevent, a number of these harms. We propose five principles for home robots and privacy design: data minimization, purpose specifications, use limitations, honest anthropomorphism, and dynamic feedback and participation. […]

Honoring Jessica Rich
[…] reports on data brokers, the Internet of Things, Cross Device Tracking, Big Data, mobile security, and kids’ apps. Prior to being named Director, Jessica served in a number of senior roles at the FTC, including Deputy Director of the Bureau, Associate Director of the Division of Financial Practices, and Acting Associate Director of the […]

WannaCry About Backdoors
[…] a back door in, that back door’s for everybody, for good guys and bad guys.” Strong encryption is permitted even under the 1994 U.S. law that requires phone companies to build their networks to respond to court orders. As the ACLU’s Chris Soghoian has emphasized, that law “explicitly protected the rights of companies that […]

Consumer Genetic Testing: Beginning to Assess Privacy Practices
[…] information without explicit permission, the ability to delete their information, and promises to only use the data for the expected purposes. FPF has begun discussions with a number of consumer genetics companies and hopes to share best practices guidance in the upcoming months. But before we begin, there are some useful lessons that FPF […]

Homomorphic Encryption Signals the Future for Socially Valuable Research on Private Data
[…] of a fully homomorphic cryptosystem have been dancing in cryptographers’ heads for thirty years. I never expected to see one. It will be years before a sufficient number of cryptographers examine the algorithm that we can have any confidence that the scheme is secure, but — practicality be damned — this is an amazing […]
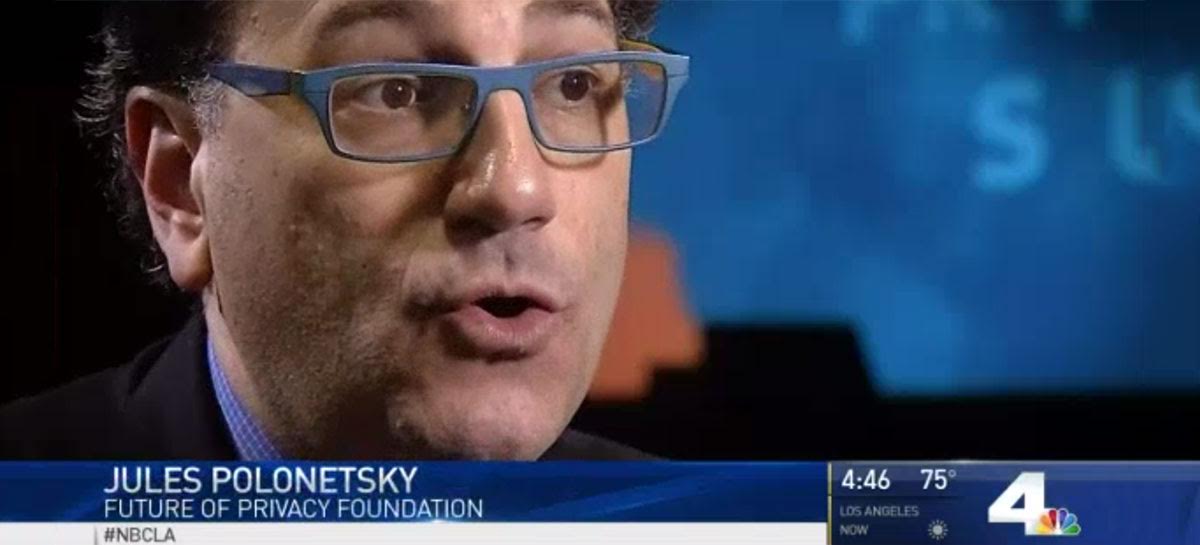
"Your Phone May Be Tracking Your Every Move; Here's How to Stop It"
During the International Association of Privacy Professional’s Global Privacy Summit 2017, FPF’s CEO, Jules Polonetsky, took a moment to speak with NBC 4 Los Angeles about the privacy implications of granting apps permission to track your location.

Privacy Scholarship Research Reporter: Issue 1, May 2017 – Algorithms: Privacy Risk and Accountability
[…] as the Shapley value, previously applied to measure influence in voting. Further, since transparency reports could compromise privacy, we explore the transparency-privacy tradeoff and prove that a number of useful transparency reports can be made differentially private with very little addition of noise. Our empirical validation with standard machine learning algorithms demonstrates that QII […]

Mobile Apps Study Underscores Necessity of Strong Best Practices for Health and Wellness Data
[…] the visual here and below. The 2016 Mobile Apps Study underscores the necessity of strong Best Practices for health and wellness data. The App Study revealed that while the number of apps that provide privacy policies continues its upward trend from our previous surveys in 2011 and 2012, health and fitness apps – which often control […]
The Privacy Policy Snapshot Challenge – $20,000 First Prize.
[…] continues its upward trend from our previous surveys in 2011 and 2012. But health and fitness apps – which may access sensitive, physiological data collected by sensors on a mobile phone, wearable, or other device – do worse than average at providing privacy policies. Only 70% of top health and fitness apps had a privacy policy (6% […]

Future of Privacy Forum Comment Regarding Senator Bill Nelson's Report, “Children's Connected Toys: Data Security and Privacy Concerns”
[…] to understand at the point of sale whether they will be asked to consent to the toy’s collection of their child’s information. Finally, the paper details a number of important security steps that leading toy manufacturers are taking; Senator Nelson’s report mentions several of these steps, for example, implementing strong security standards (HTTPS / […]
