
FPF 2024-2025 Sponsorship Prospectus Privacy Executives Summit Indivual PDF
Sponsorship levels and deliverables

FPF Sponsorship Prospectus Israel Cyber Week Individual PDF
FPF SPONSORSHIP PROSPECTUS | 6 Please contact Alyssa Rosinski at [email protected] for more information. ISRAEL CYBER WEEK FPF DELEGATION LUNCHEON SPONSOR • $5,500 • 2 available ❱ Company name and logo included in Lunch invitation and schedule of events with recognition, “Lunch brought to you by [Your Company Name]” ❱ Company name and […]

FPF Sponsorship Prospectus 2024-2025 Annual Advisory Board Meeting
Sponsorship Levels and Deliverables

FPF Sponsorship Prospectus 2024 -2025 DC Privacy Forum
Sponsorship Levels and Deliverables

FPF-Sponsorship Prospectus-24-25-R7 (1)
SPONSORSHIP PROSPECTUS 2024–2025 FPF SPONSORSHIP PROSPECTUS | 1 Please contact Alyssa Rosinski at [email protected] for more information. Why choose to sponsor with FPF? ❱ FPF brand associated with global thought leadership ❱ Access to senior-level privacy professionals with purchasing influence and authority ❱ Receive international visibility within the data protection and privacy community ❱ Ability […]

FPF Data Clean Rooms Discussion Sept 2024
Discussion Draft SEPTEMBER 2024 BY AARON MASSEY Technologist and Senior Policy Analyst for Advertising Technologies and Platforms, FPF Forward D ata clean rooms are an increasingly discussed tool in industry, utilized in advertising and marketing, health care, and academic research, as well as for regulatory compliance. Leading thinkers have already started to analyze the capabilities […]
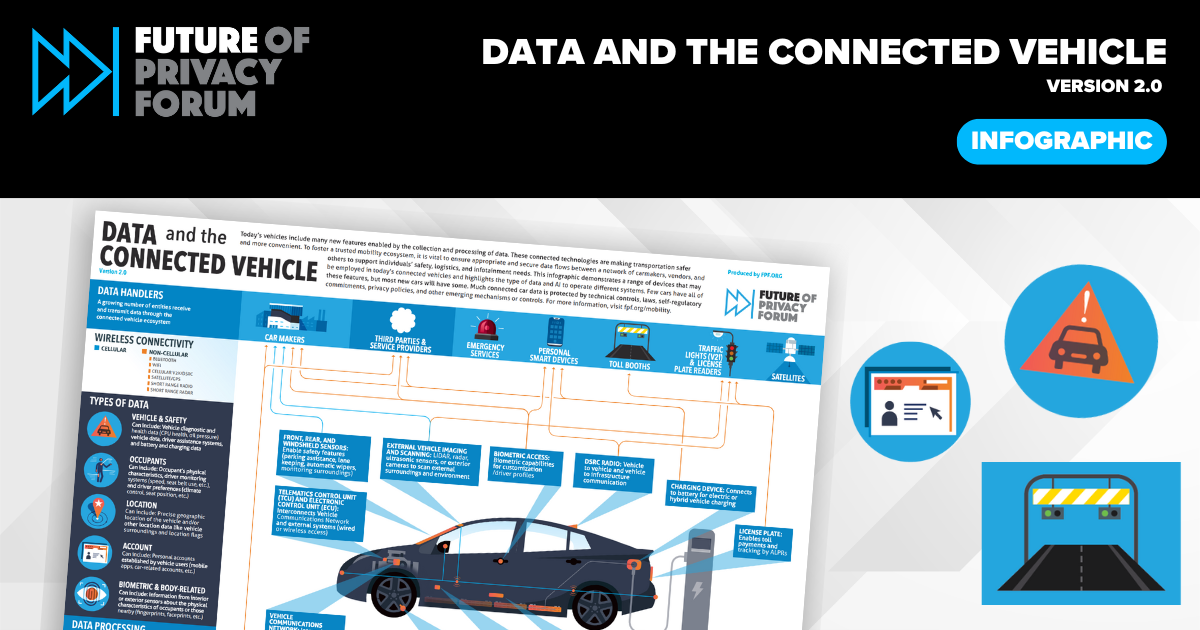
Updated FPF Infographic Explores Data in Connected Vehicles
Today, The Future of Privacy Forum is launching the Data and the Connected Vehicle Infographic 2.0, including new updates to account for the types of data associated with connected vehicles, features in and outside of the vehicle, and data handlers who receive and process data. Lawmakers, manufacturers, privacy professionals, and consumers are actively engaged in work to examine and respond […]

Updated FPF Infographic Explores Data in Connected Vehicles
Today, The Future of Privacy Forum is launching the Data and the Connected Vehicle Infographic 2.0, including new updates to account for the types of data associated with connected vehicles, features in and outside of the vehicle, and data handlers who receive and process data. Lawmakers, manufacturers, privacy professionals, and consumers are actively engaged in […]

Infographic Explores Driver Data Collection and Use in Connected Cars
FPF’s “Data and the Connected Vehicle” Demystifies Connected Car Ecosystem as Policymakers Look to Regulate SEPT. 16, 2024 — Vehicle technologies are evolving rapidly, in every facet of the system, from safety features to entertainment, and occupant convenience. Many of these new features are enabled by the collection of driver and occupant data – and […]

FPF_connected_vehicl_v2_03_nosidebar (2)
CELLULARNON-CELLULAR WIRELESS CONNECTIVITY BLUETOOTH WIFI CELLULAR V2X/DSRC SATELLITE/GPS SHORT RANGE RADIO SHORT RANGE RADAR BIOMETRIC & BODY-RELATED Can include: Information from interior or exterior sensors about the physical characteristics of occupants or those nearby (fingerprints, faceprints, etc.) ARTIFICIAL INTELLIGENCE Can include: Algorithmic processing, decision making, and machine learning present throughout various vehicle systems and features […]
