Showing results for mbines coexist secret promo code bangladesh

Best Practices
[…] by the FTC as an approved COPPA safe harbor program. Location Best Practices for Location Based Services CTIA – The Wireless Association | Mar 2010 Guidelines to promote and protect user privacy as Location Based Services are developed and deployed. Best Practices for Location Based Services Digital Signage Federation | Mar 2010 Guidelines to […]

Protected: Protected: Future of Privacy Forum’s 2020 Annual Meeting
There is no excerpt because this is a protected post.

The European Commission Considers Amending the General Data Protection Regulation to Make Digital Age of Consent Consistent
[…] ages of digital consent, there are also differing interpretations of the obligations on information society services regarding children. For example, the United Kingdom’s proposed Age Appropriate Design Code defines a child as a person under the age of 18 and lays out additional requirements for information society services to build in privacy by design […]

What to Expect from the Court of Justice of the EU in the Schrems II Decision This Week
[…] there is no immediate solution to provide an alternative lawful mechanism for transfers. The other options provided by the GDPR, like Binding Corporate Rules, certification mechanisms and Codes of Conduct (CoC) take a long time to be approved by Data Protection Authorities and very few are in place (particularly BCRs; there are currently no […]

Jules Polonetsky
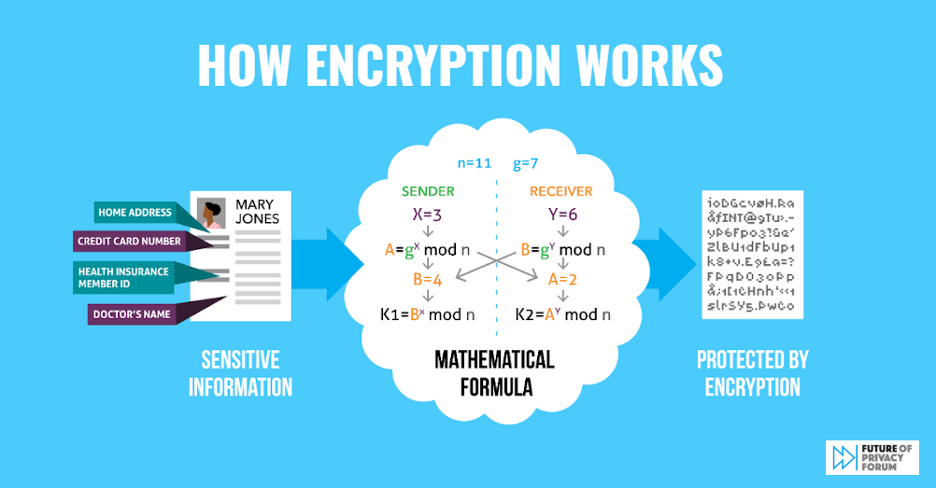
Strong Data Encryption Protects Everyone: FPF Infographic Details Encryption Benefits for Individuals, Enterprises, and Government Officials
[…] encryption generates a very long number that is the mathematical solution to the formula and can unscramble the protected sensitive information. This “key” must be kept a secret or anyone who has it will be able to access the information. Strong encryption employed by online services and connected devices protects sensitive communications and stored […]

iOS Privacy Advances
[…] the data is linked to a particular user or device, and if the data will be used to track users. Because SDK’s run in-process with other app code, and share the app’s access permissions, developer responses are required to reflect both the practices of the app as well as any 3rd party code within […]

Privacy Scholarship Research Reporter: Issue 5, July 2020 – Preserving Privacy in Machine Learning: New Research on Data and Model Privacy
[…] encrypted and decrypted without loss, represents a particularly unique challenge and opportunity for creativity. One way in which images can be shared more securely is by using secret sharing protocols, which require a combination of small pieces of secret information until a threshold of secret bits is compiled at which point a secret, such […]

Commoditization of Data is the Problem, Not the Solution – Why Placing a Price Tag on Personal Information May Harm Rather Than Protect Consumer Privacy
[…] consumers are not the product, but rather “Angel Au-Yeung, “California Wants to Copy Alaska and Pay People a ‘Data Dividend.’ Is It Realistic?” Forbes(Feb. 14, 2019), https://www.forbes.com/sites/angelauyeung/2019/02/14/california-wants-to-copy-alaska-and-pay-people-a-data-dividend–is-it-realistic/#30486ee6222c. Cal. Civ. Code § 1798.125(b)(1) (“A business may offer financial incentives, including payments to consumers as compensation for the collection of personal information, the sale of personal information, or […]

Remarks on Diversity and Inclusion by Michael McCullough
[…] and build zero discrimination coding and design), /// measure it and seek feedback internally and externally. Defang an inarguably unfair and institutionally white supremacist carceral system by promoting programs and focusing on giving formerly incarcerated a hand up. Go beyond including diverse images in your spaces; seek out and ensure diverse image makers and […]
