Showing results for feifei phone number 1800 299 964 fpfgw 282 fpfgw 283 fpfgw 282 fpfgw 283 fpfgw 282 fpfgw 283 fpfgw 254 fpfgw 283 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 275 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 283 fpfgw 282 fpfgw 283 fpfgw 282 fpfgw 283 fpfgw 254 fpfgw 283 fpfgw 282 fpfgw 283 fpfgw 282 fpfgw 283 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 275 fpfgw 254 fpfgw 283 fpfgw 254 feifei phone number 860 490 8326 1800 299 964 ___ 860-490-8326 number 1800 299 964 fpfgw 282 fpfgw 283 fpfgw 282 fpfgw 283 fpfgw 282 fpfgw 283 fpfgw 254 fpfgw 283 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 275 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 283 fpfgw 282 fpfgw 283 fpfgw 282 fpfgw 283 fpfgw 254 fpfgw 283 fpfgw 282 fpfgw 283 fpfgw 282 fpfgw 283 fpfgw 254 fpfgw 275 fpfgw 254 fpfgw 275 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 277 fpfgw 296 fpfgw 275 fpfgw 254 fpfgw 283 fpfgw 254 number 860 8326 1800 299 964 1800 299 964 282 283 282 283 282 283 254 283 254 275 254 275 296 275 254 275 296 275 254 275 254 275 296 277 296 277 296 275 296 277 296 277 296 275 254 275 254 275 254 283 282 283 282 283 254 283 282 283 282 283 254 275 254 275 296 277 296 277 296 277 296 275 254 283 254 860 490 8326 1800 299 964
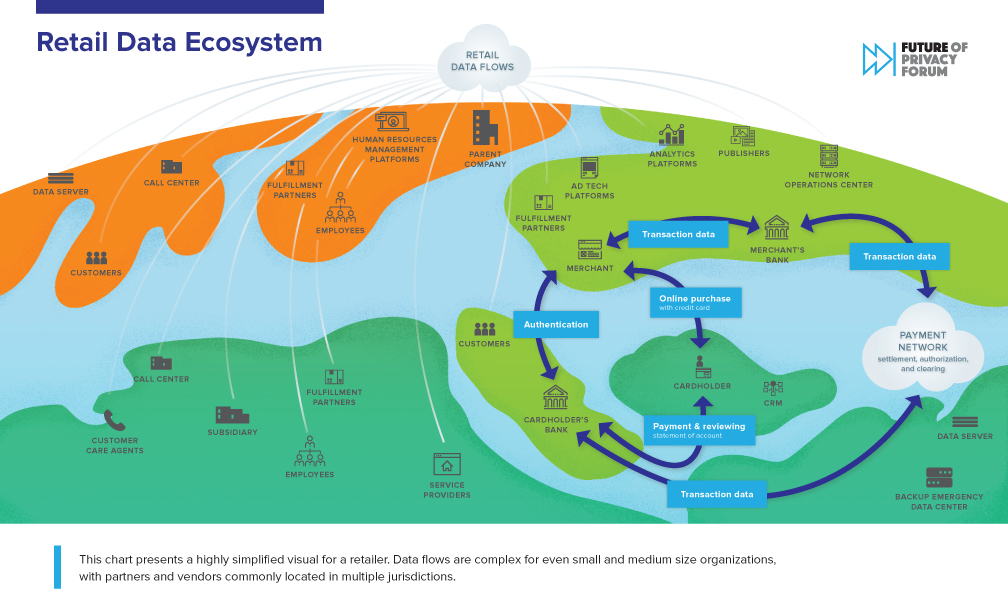
Understanding Interconnected Local and Global Data Flows
[…] Data flows are complex for even small and medium size organizations, with partners and vendors commonly located in multiple jurisdictions. A retailer is likely to use a number of different cloud-based service providers to support consumer transactions. Many of these service providers may only be located in a single jurisdiction and be geographically dispersed. […]

Emerging Patchwork or Laboratories of Democracy? Privacy Legislation in Virginia and Other States
[…] consumer, or by a person to whom the consumer has disclosed the information, unless the consumer has restricted the information to a specific audience.” In addition, a number of exemptions are currently drafted in the bill, including for: government entities; non-profits; data collected in the employment context; covered entities in regulated sectors, including: data […]

Seven Questions to Ask if You Have XR on Your Holiday Wish List
[…] In-product purchasing can add further details to an XR user’s profile, preferences, and interests. Some XR providers share personal data with subsidiaries and third parties for a number of purposes—from improving content and informing future updates to using XR data for advertising and recommendations for online content. 3. Ok, but what does that mean […]

The Complex Landscape of Enforcing the LGPD in Brazil: Public Prosecutors, Courts and the National System of Consumer Defense
[…] Attorney General of the Republic, there is no irrelevant data in this day and age, and even personal data that may seem trivial, such as individuals’ names, phone numbers and addresses, deserve constitutional protection from abuse. The decision notably took influence from the European Charter of Fundamental Rights. Another recent case discussed the implications […]
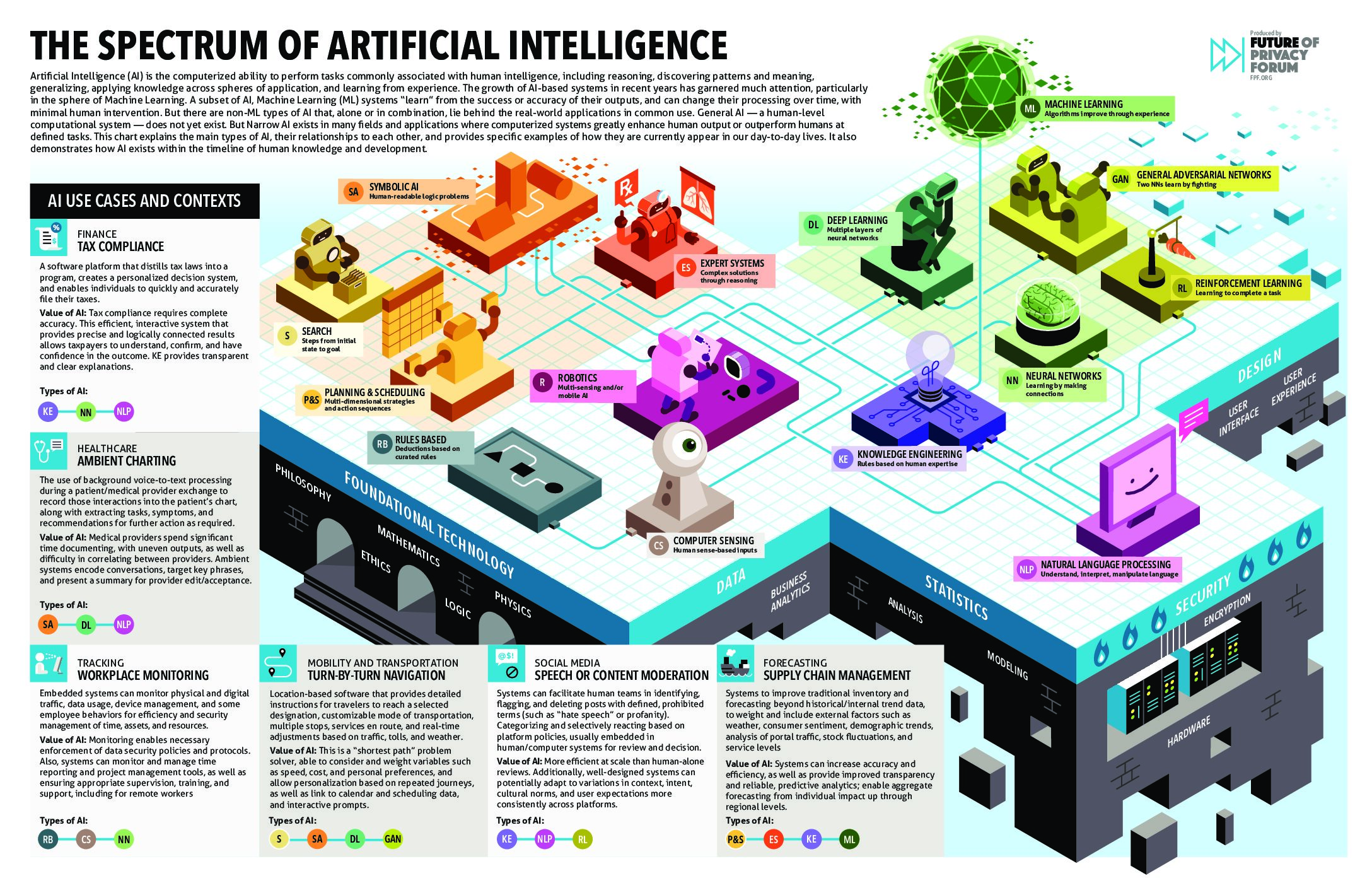
The Spectrum of Artificial Intelligence – An Infographic Tool
[…] Networks, Reinforcement Learning, and General Adversarial Networks (GANs) To aid in understanding these various types of AI programming, we have highlighted a specific use case in a number of broad topic areas. Finance – Tax Compliance programs that allow you to fill out your tax forms and ensure your information included and provided in […]
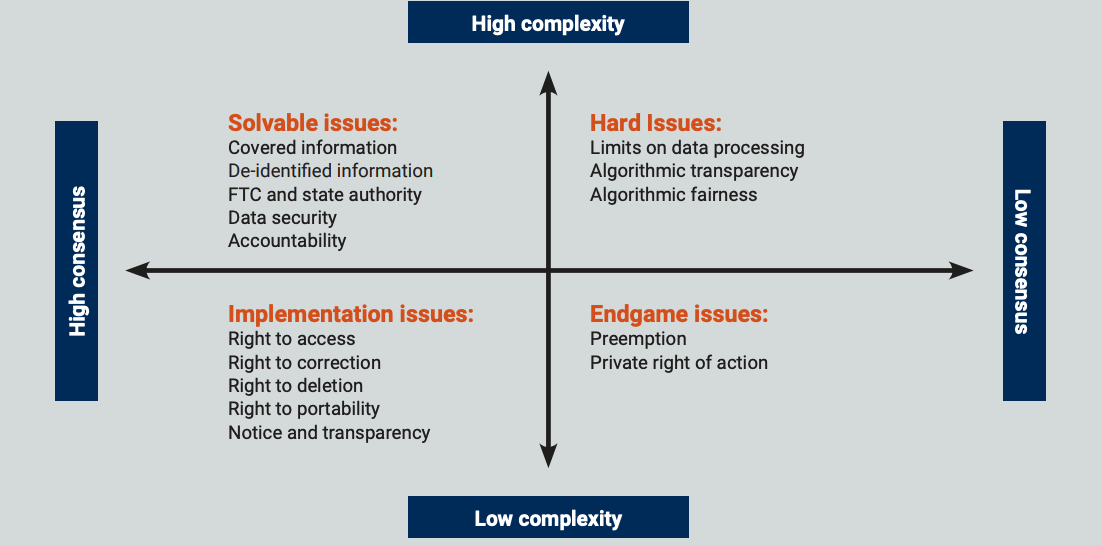
Legislative Findings: Brookings Builds on U.S. Privacy Legislation Report
[…] goals that legislators are trying to achieve through the legislation. The articulation of the foundational principles and aims of privacy legislation is powerful and important for a number of non-operational reasons. These include building support among the public and members of Congress, declaring American values to the world, informing judicial and agency interpretation, and […]

A Deep Dive into New Zealand’s New Privacy Law: Extraterritorial Effect, Cross-Border Data Transfers Restrictions and New Powers of the Privacy Commissioner
[…] enforced through the Tribunal, and a failure to comply is a criminal offense, resulting in fines up to $10,000 New Zealand dollars. The Commissioner will consider a number of factors prior to issuing a compliance notice to an entity, such as the seriousness of the breach, the number of people affected, and the likely […]

Understanding Blockchain: A Review of FPF’s Oct. 29th Digital Data Flows Masterclass
[…] related information was included in the transaction as stored on the chain. However, as the underlying technology has been considered for other uses, there have been a number of changes to that design. Distributed ledgers are now created in ways that can be private, public or hybrid in nature. Public ledgers operate as an […]

Event Recap: Panel at the Annual Privacy Forum 2020
[…] that there are many different tracking techniques and mechanisms, e.g., monitoring web traffic through cookies, tracking across devices, using the Media Access Control (MAC) address of mobile phone to pinpoint geolocation, and utilizing Wi-Fi Access Points in public areas like airports or train stations. Such complexity has raised profound questions around how regulators can […]

FPF & Dataskydd.net Webinar – Privacy in High Density Crowd Contexts
[…] patterns of commuters with an alternative method that masks the identities of the passengers. Dutch Railways does this by hashing twice the WiFI-MAC address of the traveler’s phone through sensors in the railway station and sending the data to a central server. During the length of commute, subsequent sensors send hashed information to the […]
