Showing results for housin call 614 647 0039 electrical repair services housin call 800 387 0073 614 647 0039 1-800-387-0073 call 614 647 0039 call 1 0073 614 647 0039 614 647 0039 800 387 0073 614 647 0039
FPF Submits Comments to Inform New York Children’s Privacy Rulemaking Processes
[…] bills aimed at creating heightened protections for children and teens online. One, the New York Child Data Protection Act (NYCDPA), applies to a broad range of online services that are “primarily directed to children.” The NYCDPA creates novel substantive data minimization requirements, restricts the sale of data of children (defined as under 18), and […]

FPF-Sponsorship Prospectus-24-25-R7
[…] benefits for the above Coffee Breaks & Networking Lunch Sponsorship included ❱ Name, logo, and website link on event page, located on FPF website, with a special call-out as the exclusive sponsor FPF DC PRIVACY FORUM FPF SPONSORSHIP PROSPECTUS | 4 Please contact Alyssa Rosinski at [email protected] for more information. FPF ANNUAL […]

FPF Sponsorship Prospectus 2024 -2025 DC Privacy Forum
[…] located on FPF website ❱ Official recognition of sponsor during Opening Remarks EXCLUSIVE FORUM SPONSOR • $12,000 ❱ All benefits for the above Coffee Breaks & Networking Lunch Sponsorship included ❱ Name, logo, and website link on event page, located on FPF website, with a special call-out as the exclusive sponsor FPF DC PRIVACY FORUM

FPF-Sponsorship Prospectus-24-25-R7 (1)
[…] benefits for the above Coffee Breaks & Networking Lunch Sponsorship included ❱ Name, logo, and website link on event page, located on FPF website, with a special call-out as the exclusive sponsor FPF DC PRIVACY FORUM FPF SPONSORSHIP PROSPECTUS | 4 Please contact Alyssa Rosinski at [email protected] for more information. FPF ANNUAL […]

Data Clean Rooms: A Taxonomy & Technical Primer Discussion Draft
1970-01-01 01/01/1970 January 1, 70

FPF Data Clean Rooms Discussion Sept 2024
[…] the product. All personnel and equipment entering a silicon fabrication facility must ensure they are not contaminating the facility. To that end, personnel wear cleanroom suits, also called “bunny suitsâ€, which ensure no outside contaminant affects the delicate manufacturing inside the facility. Thus, “clean room†originally referred to a place where everything was clean, […]
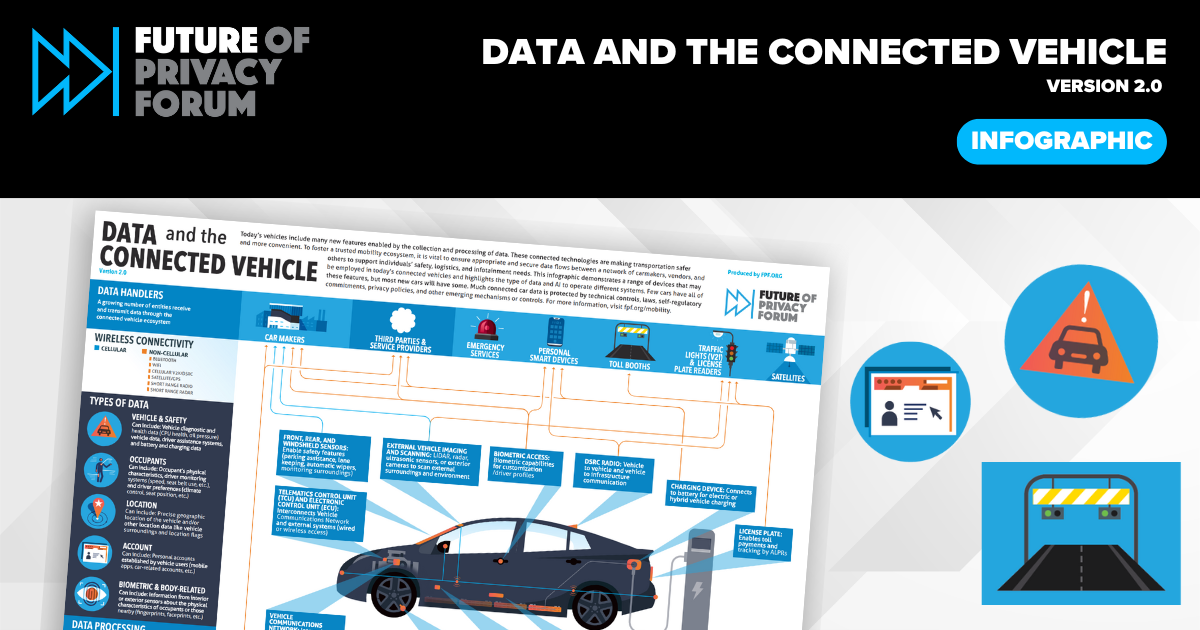
Updated FPF Infographic Explores Data in Connected Vehicles
[…] Once the data is collected, its transfer and use can depend on a number of factors, including agreements with the manufacturer, third parties and service providers, emergency services, and external infrastructure such as traffic lights and automatic license plate readers. Manufacturers may receive vehicle and safety data, location data, account data, occupant data, and […]

FPF_connected_vehicl_v2_03_nosidebar (2)
[…] entities receive and transmit data through the connected vehicle ecosystem DATA HANDLERS TRAFFIC LIGHTS (V2I) & LICENSE PL ATE READERS PERSONAL SMART DEVICES TOLL BOOTHS SATELLITES EMERGENCY SERVICES © 2024. This work is openly licensed via CC BY 4.0. and the Today’s vehicles include many new features enabled by the collection and processing of […]

FPF Unveils Report on Emerging Trends in U.S. State AI Regulation
1970-01-01 01/01/1970 January 1, 70
